BFTP: In praise of late adopters
 Sunday, January 31, 2016 at 05:52AM
Sunday, January 31, 2016 at 05:52AM I've decided to come out of the closet.
No, no, not that closet. But I need to fully confess that I am a confirmed "late adopter." No more subterfuge, no more denial, no more embarrassment.
I am out and proud of my foot-dragging tendencies when it comes to personal technologies.
Most of us are familiar with the Rogers "Technology Adoption Lifecyle" popularized by Geoffrey Moore in his book Crossing the Chasm. (Info and graphic below are from Wikipedia.)
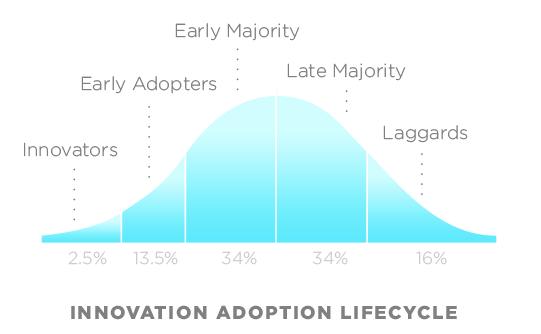
The original model was based on a study of farmers who adopted new agricultural methods. Rogers described the groups as:
- innovators - had larger farms, were more educated, more prosperous and more risk-oriented
- early adopters - younger, more educated, tended to be community leaders
- early majority - more conservative but open to new ideas, active in community and influence to neighbours
- late majority - older, less educated, fairly conservative and less socially active
- laggards - very conservative, had small farms and capital, oldest and least educated
Moore and others saw this curve with all technology adoptions.
Why am I suddenly identifying with the "older, less educated, fairly conservative and less socially active" group, Well, I recognize that it does increasingly fit my description. As the t-shirt says, I'm "over the hill and picking up speed."
But really it's because last week I got completely disgusted at having five different goddam ends for five goddam different devices that need to be charged.
- My cell phone
- My 3G wireless router
- My iPad
- My Kindle
- My laptop
I got more cords than a Wurlitzer organ. (Or maybe that should be chords.)
I am quite sure others in my late adopter peer group will not have to deal with this charger nonsense; that a common "tip" for all devices must be on the horizon. All good things come to those who wait.
This lack of consistency is just one thing that makes sane people drag their feet about any technology adoption. Why should a busy teacher need to remember what charging cord goes to what do-hickey and carry a bag-full of them around?
Educational leaders (innovators) spend a lot of time encouraging and persuading the early adopters and even the early majority, but few pay much attention to those of us who want to make darned sure the time, effort and expense of doing something new is worth it.
We late adopters add stability to institutions in a world that changes at an unsettling rate. We demand hard evidence that the new thing is also the better thing. We recognize that there is value in some aspects of the status quo. We are more than happy to let others be on the bleeding edge and have the kinks all worked out of the system by the time we get to the new technology.
Here's my advice for getting those of us in the back of the line on the tech bus...
- Make sure it works flawlessly, every time.
- Make sure it really saves me time or makes me more productive.
- Make it as transparent as possible.
- Don't make me use so many steps I've got to write them down or keep a manual by my side.
- Have plenty of endorsements about your technology from building-level practitioners - not starry-eyed visionaries.
- Don't make me get a different charger.
Join me for Late Adopter Pride Week. I'll let you know when it is. If ever.











